Posted on August 25, 2022
Estimated reading time 5 minutes
Cybersecurity threats are constantly evolving, and your business is at risk if you do not implement measures to protect your information assets. A security operations centre (SOC) is a centralised organisation that monitors and eliminates cybersecurity threats to IT networks.
Managed security operations services offer you 24/7 support in identifying and remedying cybersecurity breaches and IT vulnerabilities in your organisation.
This article will outline the critical components of all reputable SOC managed service providers like Atech. We’ll also explore how you can better protect your business by deploying the best people, technologies, and processes to manage cyber-attack risk.
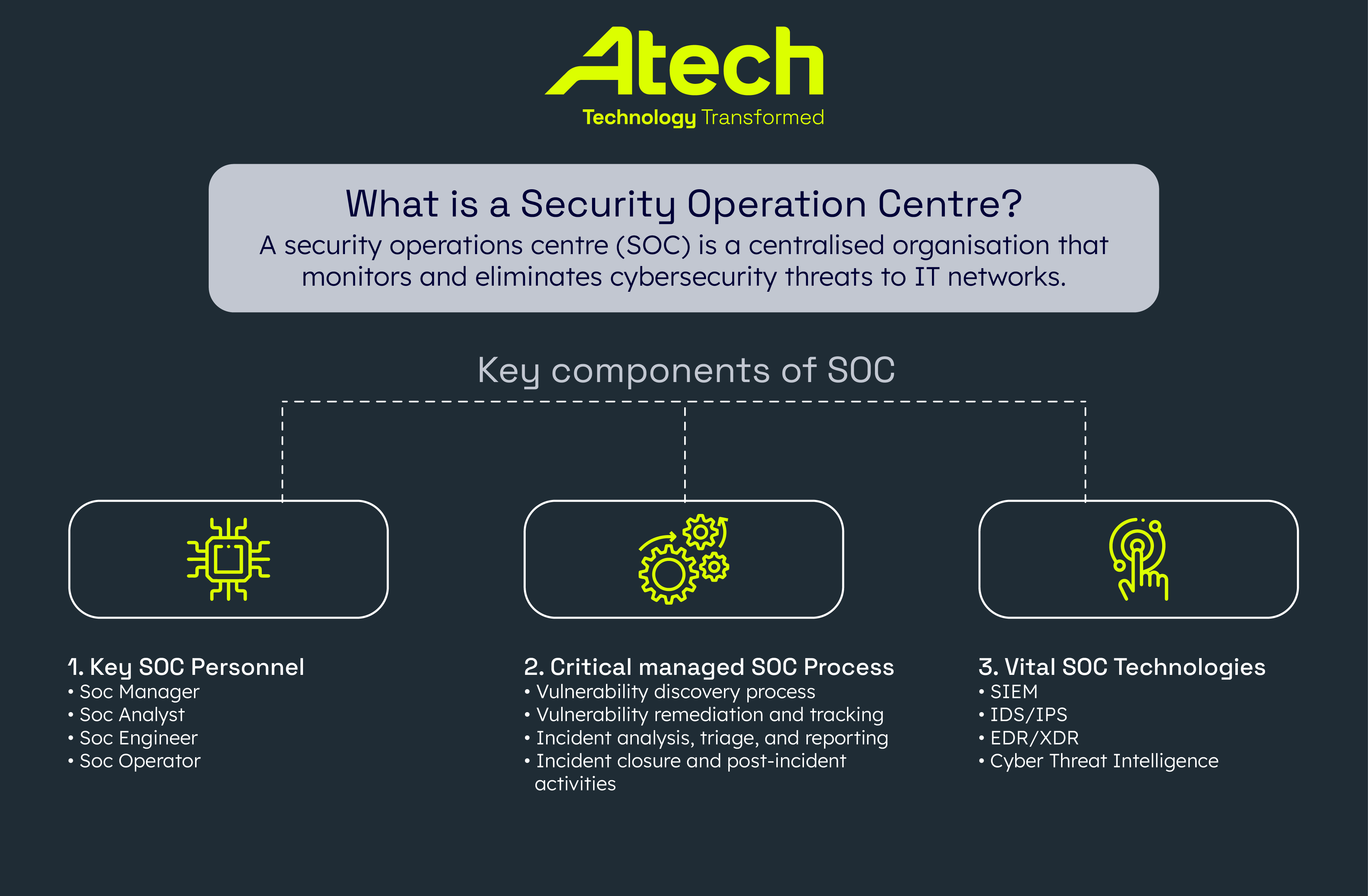
What is a Security Operations Centre?
SOCs have extensive expertise in securing enterprise systems, large and small. They can offer advice and technological solutions to help brands improve their IT efficiency and enhance their technical abilities while maintaining tight information security indefinitely. The best SOC services can also help businesses unlock their growth potential, cut down on unnecessary IT spending, and be a real asset to an organisation’s development.
The main components of SOCs
Successful SOC companies embody the perfect mix of people, processes, and technologies to help deliver proactive defence and security remediation services. Each component is as vital as the next in building and maintaining a robust cyber protection strategy.
Here, we will go into more detail on how SOC processes, technologies, and personnel all work together to keep cyber threats at bay.
1. Key SOC personnel
Many roles within the SOC are intrinsic to the operation’s success. They include;
- SOC Manager – The SOC manager takes the lead on all projects and manages the entire security operation to ensure all projects align with strategic KPIs.
- SOC Analyst – Analysts are the heart of the SOC, as they’re responsible for consistently monitoring cybersecurity threats across networks. They also analyse and report on all security data within an organisation.
- SOC Engineer – The lead SOC engine selects and installs the technologies that will protect companies from cyber threats. SOC engineers need to keep their fingers on the pulse of cybersecurity developments to devise new methods to stop cyber criminals in their tracks.
- SOC Operator – SOC operators are responsible for maintaining the SOC tools to ensure they run optimally.
All the above roles require specialised skills in creative problem-solving, pattern recognition, and a great deal of dedication in delivering a high level of service to clients.
2. Critical managed SOC processes
Managed SOC services rely on an extensive list of procedures to fortify systems and devices on behalf of their enterprise customers. Here, we will run through a brief list of typical duties SOCs must execute on a regular basis to safeguard IT systems.
- Vulnerability discovery process – The first stage in securing any network is scanning all activity and identifying any vulnerabilities. Once any issues are identified, the discovery process involves grading vulnerabilities by severity and deciding the best course of action.
- Vulnerability remediation and tracking – Vulnerability tracking and remediation activities are the processes that aid SOC teams in targeting and removing threats from systems. These activities rely on open communication channels between SOC staff to help them track and fix issues as soon as possible.
- Incident analysis, triage, and reporting – The primary duties of a SOC analyst are to analyse security incidents. Analysts are adept at detecting the root cause of vulnerabilities and figuring out the best way to contain threats before they become a problem.
- Incident closure and post-incident activities – After a vulnerability is fixed, incident closure procedures begin to verify that the threat has been effectively terminated. Managed SOC teams must also test and ensure the systems’ weaknesses no longer exist. Post-incident activities also include information-gathering tasks establishing the lessons learned from the threat and how remedies may be applied in future incidents.
Atech’s enhanced SOC services
In addition to the processes listed above, Atech clients enjoy managed security services that enhance the capabilities of its IT infrastructure. For example, our endpoint, information, and identity protection services enable organisations to collaborate and work from anywhere securely – without getting bogged down with overly complicated security protocols.
We use Microsoft Defender for Endpoint and Azure Information Protection (AIP), Defender for Identity, Defender for Cloud Apps, Azure Rights Management (Azure RMS), and Azure AD Identity Protection, Defender for Office 365. Our pure-play Microsoft SOC approach equips us with the ideal-fit tooling for evaluating, managing, and storing all enterprise information safely in the cloud. The integration of Microsoft 365 Defender with Sentinel translates as visibility of all threats and incidents, and the ability to perform investigation in Sentinel in near real time and subsequently decide on remedial action. Enriching and grouping alerts from multiple 365 products, means the time to resolve is shortened, and the insights gained ensures a more proactive posture can be attained.
3. Vital SOC technologies
We have touched upon a few technologies used to maintain smooth SOC processes. Now we will take a closer look at a few specialised SOC technologies designed to keep enterprises secure at all times.
- SIEM – A Security Information and Event Management (SIEM) platform uses real-time and historical data to detect, mitigate and comply with threat management protocols. It can also collect and analyse contextual data from numerous sources.
- EDR/XDR – Endpoint Detection & Response (EDR) and Extended Detection & Response tools help to detect suspicious activity across your endpoints. A SOC analyst studies and reports on EDR and XDR data.
- IDS/IPS – Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) continually monitor all network activity. It is used in identifying and logging information about potentially suspicious activity. The software will then report its findings to analysts.
- Cyber Threat Intelligence – Threat intelligence tools gather and analyse cybersecurity information from external sources. This technology shores up an enterprise system’s security posture ahead of any future risks.
SOC Managed services keep you one step ahead of online threats
Managed services SOCs give your enterprise the tools it needs to ensure continuity and its continued expansion over the long term. It helps businesses ensure flawless data governance and control of all information coming into and circulating within your organisation.
The best managed security services SOCs take a three-tiered approach to defend your assets, including; endpoint, information, and identity protection strategies. They also incorporate cutting-edge technologies and pragmatic problem-solving abilities built on decades of experience to bring unparalleled levels of security to your organisation.
Atech are a pure-play Microsoft SOC with full remediation capabilities
Atech’s managed security services SOC is built with the latest Microsoft SOC tools. We offer full remediation capabilities, enabling you to fortify your business from cyber threats as you grow.
We were also named Finalists in Microsoft’s Partner of the Year Awards 2022 for Endpoint Management. We protect over 45,000 devices worldwide and help businesses defend billions of pounds worth of assets – 24/7, 365.
Get in touch. if you want to learn more about how Atech can offer you the best security operations centre services.