Posted on November 29, 2023
Estimated reading time 5 minutes
In the ever-evolving threat landscape, many organisations overlook the security features already available to them in the Microsoft 365 subscription, choosing instead to invest in additional third-party security and compliance tools that ultimately make their IT estate harder to manage and may leave gaps in your security posture.
Here at Atech, we’re committed to helping you optimise your security posture for less cost and management overhead by empowering you to realise more value from your existing licensing investment.
On Tuesday, 28th November 2023, we hosted an in-depth Microsoft 365 Security webinar featuring Hope Chauland, Microsoft’s Go-To-Market Lead for Identity and Access Management, alongside Atech’s Head of Security, James Pearse, and Microsoft Product Marketing Manager, Elaine Riley.
Together, we’ve identified what you need to know about harnessing the full potential of your Microsoft 365 Security investment – from consolidating licensing costs to future-proofing your IT security from ever-increasing threats.
If you missed out on the live event, don’t worry; this blog summarises the webinar’s key takeaways and provides more information on how Atech can help you understand the true value of your Microsoft 365 Security Suite. You can also watch a playback of the full webinar here
Atech’s Microsoft 365 Security webinar agenda
Item #1: The value of configuration and vendor consolidation
We began by outlining common issues organisations face when it comes to improving their security posture, including:
- A lack of understanding in the many Microsoft 365 Security features included in every subscription.
- The challenge organisations face with 50% of all UK businesses having both a cyber skills and competency shortage.
- Squeezed IT budgets because of over-investment in unnecessary third-party security tools.
- Lack of security insight, as organisations struggle to manage a diverse set of security tooling.
However, by consolidating IT security providers, we explained how you can unlock further cost savings, streamline security management, and reduce your threat surface overall.
Item #2: Microsoft 365 Security capabilities
To further demonstrate the value of embedded Microsoft 365 Security capabilities, we ran through some common instances of duplication and highlighted some examples where our clients had deployed unnecessary tools running alongside their Microsoft 365 investment:
- Mimecast: Our clients had often deployed Microsoft 365 alongside Mimecast. Organisations are generally unaware of the capabilities within Microsoft Defender XDR that replaces the need for Mimecast.
- Okta: Often a legacy deployment that organisations have installed in the past to manage and maintain identity multi-cloud and hybrid environments. Microsoft’s recent expansion of the EntraID suite, delivers enhanced Identity compliance and governance platform for Azure, on-premises, and multi-cloud environments.
- Jamf: Microsoft Intune has the capabilities and features to replace most instances where Jamf has been deployed. Intune supports multi-platform features, removing the need for additional tools to manage devices not running on Windows.
- Carbon Black: Microsoft Defender for Endpoint provides unified and agentless Endpoint Detection Response (EDR) and is integrated within the Defender XDR platform, providing a single pane of glass management solution.
Item #3: Security value calculator
The webinar highlighted the need for organisations to ensure ROI on IT security investments. So, we showcased the Microsoft ROI Value Calculator and provided examples of how vendor consolidation saves organisations significant time and costs in managing security.
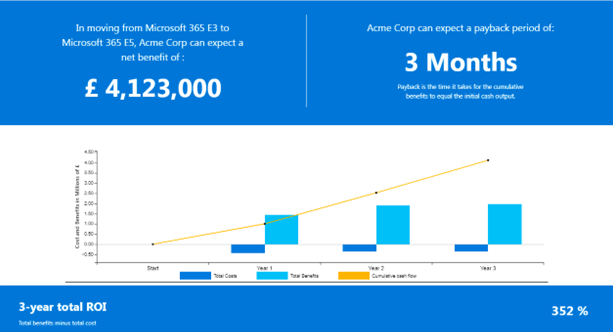
For example, pairing a Microsoft 365 E3 subscription with its E5 security add-on can deliver 352% ROI over three years (based on the example given in the webinar)
Item #4: The current threat landscape
Next, we explored in more detail exactly how decentralised security weakens IT security.
For example, Hope highlighted that when you utilise multiple security tools, the attack chain is covered by technology that shares no information or context of what has happened elsewhere in the kill chain.
“This complexity and lack of cohesion frequently results in a delay in the detection time and a lack of automated response. Having to perform investigations and forensics across the entire stack is manual, time-consuming and, most importantly, it continues to be damaging until disruption and containment are complete.”
The benefit of Microsoft Defender XDR is that all of this “stitching” is already done, reducing the management and development overhead.
Item #5: Activation and consolidation of security applications
In this webinar segment, we demonstrated how Atech works with you to activate and consolidate your security applications.
First, we provided a series of one-to-one workshops to help us draw a clear picture of your security environment.
Next, we developed a detailed plan for optimising the Microsoft 365 Security tools you already have, as well as plans for decommissioning your redundant tools.
Throughout the process, and after the transformation is complete, we provided regular project health checks to ensure you’re satisfied, and your systems remain secure.
Item #6: Atech Case Study
Finally, we put all the webinar’s valuable information into context with examples of how best to get started with our range of assessment and workshops.
All the details of our various engagements can be found here: https://atech.cloud/workshops/
Atech: Your partner in maximising IT Security investments
We want to thank our speakers for participating and our live viewers for tuning into the webinar.
If you would like to learn more about how you can unlock your path to greater security success with Atech, download this information sheet or get in touch for a one-to-one Microsoft 365 Security Assessment workshop.